Docker owes much of its popularity to the fact that it removes hurdles for developers who need to distribute their software. Pairing it with Kata Containers can make it even more secure.
Kata Containers is an open-source project and community working to build a standard implementation of lightweight Virtual Machines (VMs) that feel and perform like containers, but provide the workload isolation and security advantages of VMs.
Nils Magnus, a cloud architect at Open Telekom Cloud, ran a recent hour-long webinar (the recording is free with email registration here) on how Kata can improve Docker security. It includes a demo installation of Kata and Docker containers, plus how to configure them and verify that they’re up and running.
Here are the main sections of the webinar, along with their timestamps:
• Overview of containers (at the 9:45 mark), Docker and Kata architecture (15:01)
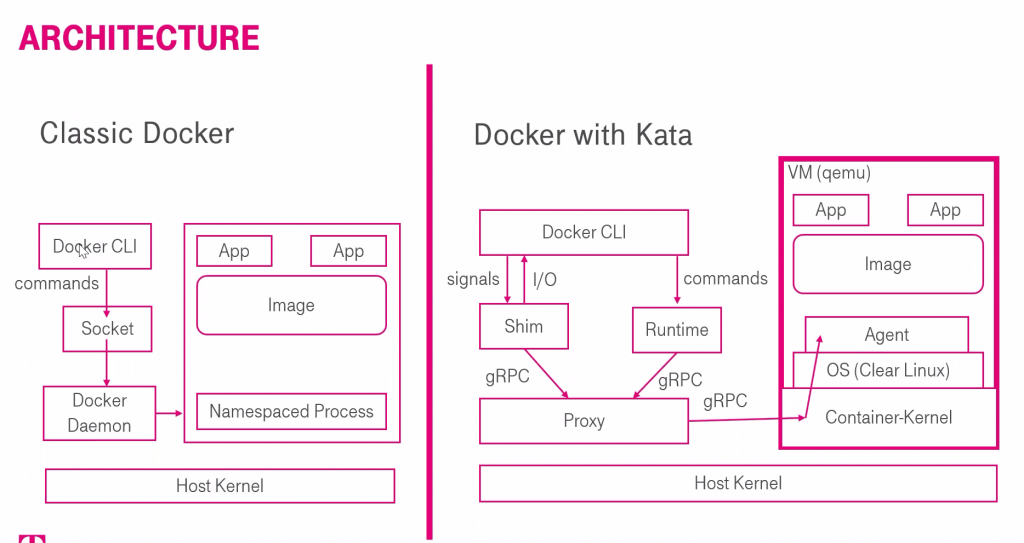
• Installation (30:32) on a bare metal server at Open Telekom Cloud with 16 cores and 256 GB, though Magnus says it’s not necessary to run the demo, he wanted to show it on a “decent machine” with capabilities for running several hundred containers.
• Configuration (37:04), verification (39:00), containers in action (40), inside the VM (41:29), troubleshooting commands (42:36). The scripts used in the demo for the automated installation and simple benchmark of the Kata Container runtime are available on GitHub.
• Performance benchmarks (47:06) and results (49:17)
• Use cases (50:10)
So just what are the security advantages? “In a situation where you have several classic Docker containers running and one of your apps has some vulnerabilities and an attacker can access one of the apps inside one of your containers. If the hacker can identify some vulnerabilities in the host kernel, they could access whole system itself of another one of the containers – an isolation breach.” In Kata Containers, it’s different, Magnus says. “Even if we have an attacker in one of the apps and even if the kernel contains a vulnerability, the attacker wouldn’t be able to leave the VM. This is the main difference.”
As for what could be improved in the Kata-Docker pairing, some of the improvements Magnus would like to see include an improved memory footprint, further reduction of the guest Image, removal of the shim between container and runtime and further reduction of the hypervisor footprint.
Get involved
Kata Containers is a fully open-source project––check out Kata Containers on GitHub and join the channels below to find out how you can contribute.
- GitHub: https://github.com/kata-containers
- Slack: link: https://katacontainers.slack.com ; invite: http://bit.ly/KataSlack
- IRC: #kata-dev on Freenode
- Mailing list: http://lists.katacontainers.io/cgi-bin/mailman/listinfo
There are also a number of sessions featuring Kata Containers at the upcoming Open Infrastructure Summit, ranging from project onboarding to “Tailor-made security: Building a container specific hypervisor.” See all the sessions here.
- Demystifying Confidential Containers with a Live Kata Containers Demo - July 13, 2023
- OpenInfra Summit Vancouver Recap: 50 things You Need to Know - June 16, 2023
- Congratulations to the 2023 Superuser Awards Winner: Bloomberg - June 13, 2023

)










