OpenInfra Live is a new, weekly hour-long interactive show streaming to the OpenInfra YouTube channel every Thursday at 14:00 UTC (9:00 AM CT). Episodes feature more OpenInfra release updates, user stories, community meetings, and more open infrastructure stories.
The Kata Containers community hosted community members from AMD, Ant Group, Apple, IBM, and Huawei to share how they’re running Kata. Kata Containers Architecture Committee members and upstream contributors also provided an update on community development and the project roadmap.
Enjoyed this week’s episode and want to hear more about OpenInfra Live? Let us know what other topics or conversations you want to hear from the OpenInfra community this year, and help us to program OpenInfra Live! If you are running Kata Containers or helping your customers overcome the challenges discussed in this episode, join the OpenInfra Foundation to help guide Kata Containers software development and to support the global community.
In this week’s episode, Samuel Ortiz, software engineer at Apple and member of the Kata Containers Architecture Committee, kicked the episode off by talking about what’s new with the development of Kata Containers, an open source container runtime project supported by the OpenInfra Foundation.
Kata Containers Project Update
First, a quick refresher on 2.1.0 which was released on May 15. Notable features from this minor release included:
- The Kata agent that runs inside the Kata Containers guest is now asynchronous, which gives improved performance and better resource utilization
- Kata-deploy will be the main way of deploying and distributing Kata Containers
- The community went from open tracing to open telemetry
- Better direct device assignment was added
- Added support for IPv6 and virtio-mem
- Kata 1.x was officially deprecated, the first official series of the Kata Containers project
Kata 2.2.0 is the next minor release and is scheduled for August 6, but Ortiz anticipates a delay as discussed in the public Kata engineering calls. If you’re interested in learning more, he encourages you to join the community meetings.
Notable features from the Kata 2.20 release include:
- CI stabilization, which will help accelerate development and pull request merges
- Tracing improvements and stabilization
- Watchable volumes and mount points
- Moving to QEMU’s q35
The community is also simplifying release management by creating a fixed cadence, having one release candidate for the next major or minor release every three weeks. Then, there will be one minor release every 12 weeks. The contributors will use one stable branch to track the previous minor or major release progress.
Kata Container Use Cases
Within the community, there are focused discussions around Kata users’ specific issues and features. Use cases include:
- Performance isolation: best practices for keeping Kata’s resources overhead and noisiness constrained. See meeting details
- Confidential containers: running confidential computing workloads with Kata. See meeting details
Ortiz then introduced several organizations who are deploying Kata Containers to share their use cases.
Large Scale Kata Containers in Production at Ant Group
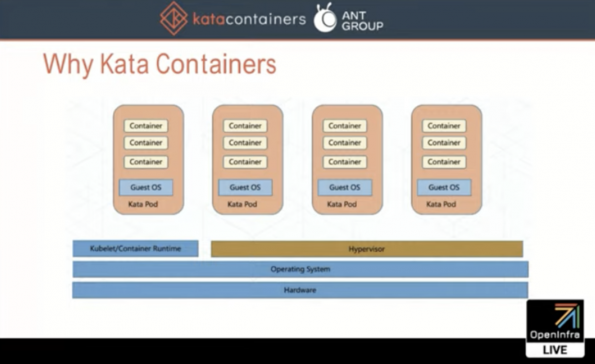
Ant Group, the leading peer-to-peer payments processor in China, does automatic online payment transactions on the world’s biggest digital payment platform all the time, so Kata Containers’ features such as isolation of network with dedicated kernels and performance jitter are critical for their use case.
“With Kata Containers, we are still sharing the same host kernel. We have a hypervisor layer and we run different pods in different guest operating systems (OS),” said Peng Tao, staff engineer at Ant Group and member of the Kata Containers Architecture Committee. “When one guest panics, it will not affect the other pods on the same host.”
With this guest OS level isolation, Ant Group no longer shares a lot of host kernel threads, allowing their service performance to be much more stable with Kata.
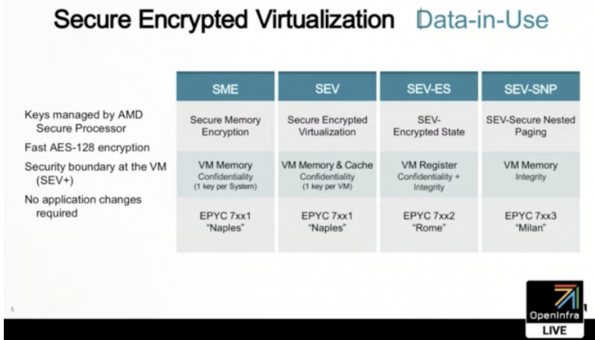
AMD Secure Encrypted Virtualization (SEV)
Brent Hollingsworth, senior manager for the EPYC Software Ecosystem team at AMD and Hubertus Franke, distinguished research staff member at IBM talked about confidential computing and the role Kata Containers plays.
With confidential computing, Franke says the customer has to have absolute trust that data is not being exposed. In regulated environments, where governments are putting stricter rules like heath data in place, it has to be ascertained that the hypervisors can get access to the data, but it sees no value in it. Encryption plays a key role so the confidential or container based workloads can be coupled with the technologies that are coming out like AMD SEV.
“With the 2018 [Kata Containers] prototype that AMD has had in place with the SEV technology, it’s been possible for us to offer confidentiality, meaning that we can turn it on and the containers would run in an encrypted mode,” Hollingsworth said. “We are currently in the process of investing in Kata Containers, we are working with the community and folks like IBM.”
Hollingsworth continued that it’s critical that in a couple of years, we have the ability to build an infrastructure that can do all of this as well as flow this to the end user so that everyone can run in a secure mode.
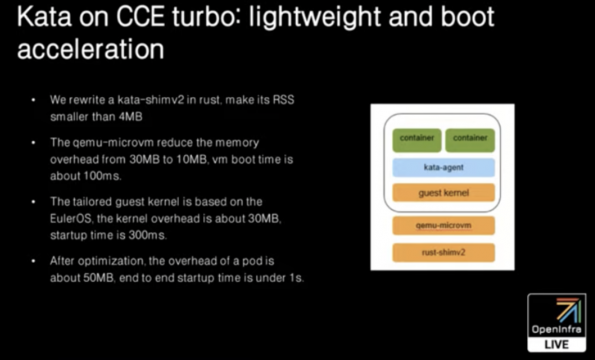
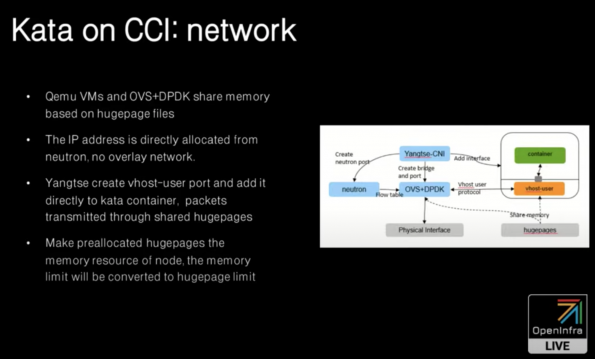
Kata Containers on Huawei Cloud
Shaobao Feng, cloud containers architect at Huawei, introduced two environments where Huawei is running Kata Containers in production: Cloud Container Instance (CCI), the first serverless Kubernetes on public cloud, and Cloud Container Engine (CCE) turbo, a complete Kubernetes service provided by the Huawei cloud.
Live Q&A Session
- What about the percent of resource utilization of the lightweight VM?
- What kind of emulation do you run?
- Are you looking at if storage direct block device is upstream able in both Kubernetes and Kata?
- Are the mentioned extensions fed back in the upstream?
Next Episode on #OpenInfraLive
The Kubernetes steering committee and OpenStack technical committee meet regularly to talk about cross-community learnings and collaboration opportunities. Join members of both governance bodies to ask questions about integration, cross-project support and how you can stay updated on the latest developments.
Tune in on Thursday, July 29 at 1400 UTC (9:00 AM CT) to watch this #OpenInfraLive episode: Kubernetes and OpenStack Working Together.
You can watch this episode live on YouTube, LinkedIn and Facebook. The recording of OpenInfra Live will be posted on OpenStack WeChat after each live stream!
Like the show? Join the community!
Catch up on the previous OpenInfra Live episodes on the OpenInfra Foundation YouTube channel, and subscribe for the Foundation email communication to hear more OpenInfra updates!
- Revolution in Cloud Economy: How FishOS – Integrated Solution Reduced Enterprise’s Cloud Costs by 50% - July 1, 2024
- Inside Open Infrastructure: June 2024 - June 18, 2024
- 2024 Superuser Awards Nominations Now Open - June 9, 2024

)







