The demand for open source is growing exponentially. But some see threats growing along with the opportunity. The fourth edition of Sonatype’s 2018 “State of the Software Supply Chain Report” offers a look at the risks and benefits. This time around, the 38-page report also highlights new methods hackers are using to infiltrate software supply chains, adds analysis across languages and ecosystems as well as explores how government regulations may impact the future of software development. You can download the report, free with email registration, here.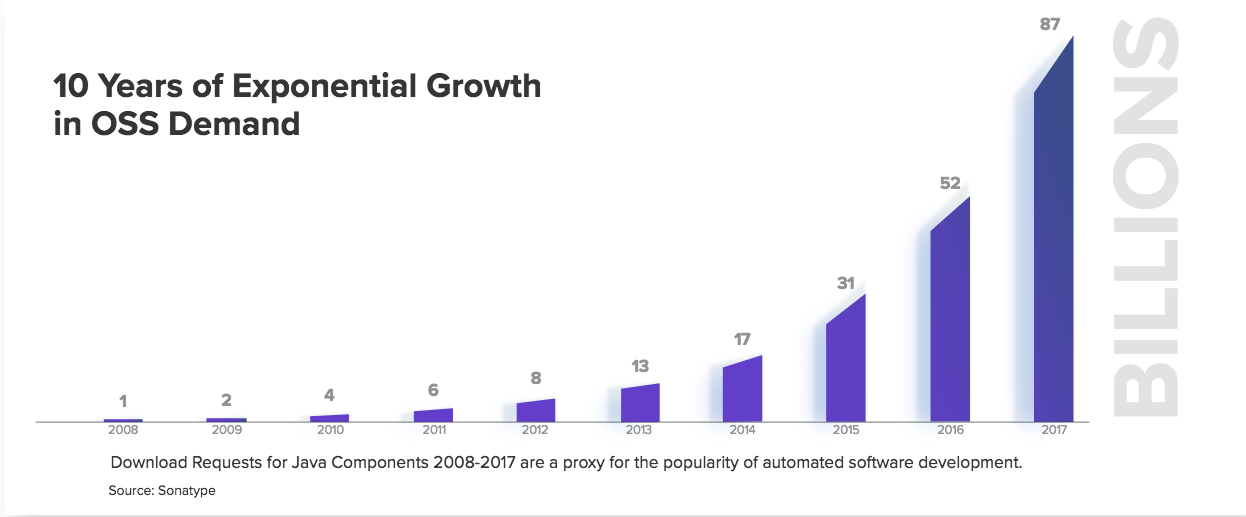
Research conducted by Sonatype shows a hockey-stick of demand for open source. Using download requests for Java components as a proxy, those requests started at a billion in 2008 and reached 87 billion in just nine years. Still, the first chapter of the report titled “We’re all Equifax” highlights a couple of key findings from their 2018 “DevSecOps Community Survey” of 2,076 IT professionals, namely that 30 percent of respondents claimed a breach stemming from the use of vulnerable open source components and that since 2014 (when Heartbleed made headlines) open-source related breaches have climbed 121 percent.
“Dev-ops-native organizations with the ability to continuously deploy software releases have an automation advantage that allows them to stay one step ahead of the hackers,” note the report authors. In a chapter dedicated to automation, the study finds that in mature dev-ops organizations, there’s bee a 15 percent year-over-year jump to 57 percent in automated security, implemented throughout each stage of the software development life cycle. The top three investments for automated security noted were web application firewalls, container security and open-source governance.
The idea of automating ahead of evil comes from Forrester’s March 2018 “Top Recommendations For Your Security Program,” where the analysts advised security teams to think about what will happen when the volume of attacks is bolstered by artificial intelligence and machine learning. Manual methods to detect, investigate and respond to threats will guarantee failure in the near future, they predict.
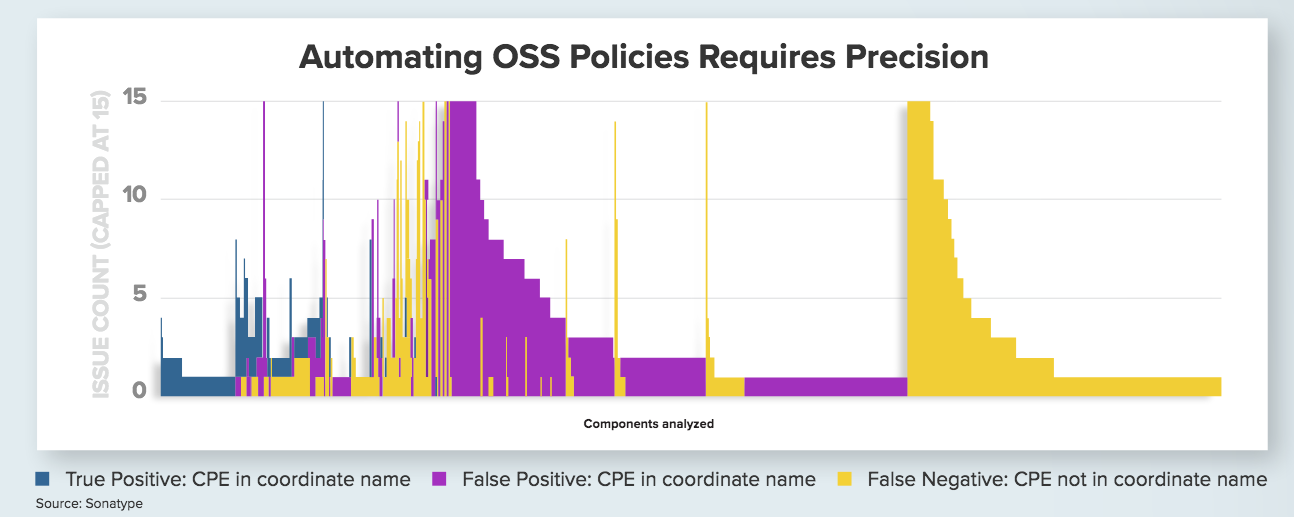
“When it comes to using open source components to manufacture modern software, the bottom line is this — precise intelligence is critical,” say the Sonotype authors. They back this up this claim with original research analyzing 6,000 open source components to understand the efficacy of CPE (common platform enumeration)- based vulnerability matching identifying 1,034 true positives, 5,330 false positives (when CPE was part of the coordinate name) and 2,969 false negatives. Crucial to stemming these problems are employing newer components and managed software supply chains, they note.
- OpenStack Homebrew Club: Meet the sausage cloud - July 31, 2019
- Building a virtuous circle with open infrastructure: Inclusive, global, adaptable - July 30, 2019
- Using Istio’s Mixer for network request caching: What’s next - July 22, 2019

)